VPN for iPhone?
 VPN for iPhone? a reader asks…
VPN for iPhone? a reader asks…
I read an article on using VPN on an iPhone (at https://www.payetteforward.com/vpn-on-an-iphone-what-is-best-vpn-for-iphone-apps-services/) – what do you think about this?
I last wrote about the VPN subject in April, check out https://positek.net/vpn-not-vpn/. But I’m going to take a fresh look at the subject, particularly in the arena of iPhones.
The article you referenced is a decent, basic primer on VPN, but I’d be real hesitant about making decisions just based on it. I wouldn’t trust any of the free VPN providers they reference, and would be hesitant about using any of the ones they recommend without a deep look into their EULA as well as their policies and privacy statements. None of the companies they list are in China or Russia, so that’s good, but I’d still research the ownership to make sure there are no suspicious… entanglements.
Here’s some relevant info:
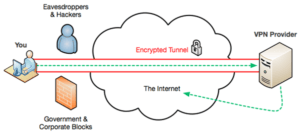
- Where a VPN really makes sense is when you’re using a public hotspot. These are notorious hangouts for hackers and they’ll often work the “man-in-the-middle” attacks which can even overcome security when surfing to a secure, https website. If you’re surfing from home or work on a secured network, you don’t have to worry about that, so a VPN really isn’t useful except for special cases (journalists in an oppressive country, hackers and others trying to hide themselves from the law, folks visiting dodgy websites, etc.).
- Using a VPN has two costs: the cost in money you pay for the service (varying from $40-100/year) and the cost in terms of slowing down your internet speed. Since all traffic has to go through the VPN provider, there is always a speed hit versus going to a website directly. There is a third cost to your time: the time and energy it takes to set it up (which can be more than you expect), and the reliability of the service, e.g., if the service you use suffers an outage.
- If you are seriously considering using a VPN, you need to invest some time in educating yourself about the threats in order to make an informed choice about which service serves your needs best. The article you referenced is only a basic primer. There’s a nice guide at https://thatoneprivacysite.net/choosing-the-best-vpn-for-you/ that will help you make better choices about which VPN service to buy. Once you have that knowledge you can use the simple comparison chart at https://thatoneprivacysite.net/simple-vpn-comparison-chart/ to narrow down the best choices, based on a color-coded threat index and your personal security concerns. The only caveat I’d include is that this privacy website is very much geared against USA-based VPN providers, which may be partly justified (based on our current administration’s direction for the FCC, etc.).
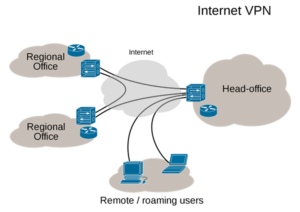
Corporate and business VPNs are pretty common, if you work for a company that uses VPN services, you should know that this is vastly different than personal use of a VPN. In a company situation, you are tunneling from one (supposedly) secure location to another. In personal use of VPN, you are going to various places on the internet.
My personal feeling is that nobody should be doing any online shopping, banking or any other sensitive activity in a public hotspot. If they have no choice, then they should use a personal Wi-fi hotspot or a good VPN service to protect themselves (basically from themselves). I carry a personal hotspot with me so I don’t have to use the services at places like Starbucks, Panera Bread, and other ‘free’ wi-fi hotspots. I don’t trust any publicly accessible hotspots anywhere including hotels – it’s too easy for a hacker to set up their own hotspot (impersonating the establishment’s) and conduct man-in-the-middle attacks, capture your internet activity and potentially hack your computer.
 Your risk to privacy and security is much more dependent on what you do (or not) than anything else. Using crappy passwords (and reusing passwords across multiple sites) is one of the easiest ways for someone to hack your digital life. When it comes to passwords, length (number of characters) is the only reasonable criteria that is worthwhile (using capital letters, numbers and other characters offers very little benefit, none if you use a short password). To be safe, you need to use a long and unique password for every online place where a login is required. By long, I mean as long as they’ll allow – certainly more than 13 characters, and I try for over 20 characters unless the website won’t allow that. No human can remember all those long passwords, so the only way to make this work is to use a password manager (my favorite is https://lastpass.com other good choices are 1Password, Dashlane, and LogMeOnce). Using a good password manager also means you don’t have to type those long passwords either since they’ll work with your web browser and auto-fill the username and password.
Your risk to privacy and security is much more dependent on what you do (or not) than anything else. Using crappy passwords (and reusing passwords across multiple sites) is one of the easiest ways for someone to hack your digital life. When it comes to passwords, length (number of characters) is the only reasonable criteria that is worthwhile (using capital letters, numbers and other characters offers very little benefit, none if you use a short password). To be safe, you need to use a long and unique password for every online place where a login is required. By long, I mean as long as they’ll allow – certainly more than 13 characters, and I try for over 20 characters unless the website won’t allow that. No human can remember all those long passwords, so the only way to make this work is to use a password manager (my favorite is https://lastpass.com other good choices are 1Password, Dashlane, and LogMeOnce). Using a good password manager also means you don’t have to type those long passwords either since they’ll work with your web browser and auto-fill the username and password.
The software development environment changes so rapidly that by the time anyone puts forward a recommendation, other products and services become available which can seriously change the equation and recommendation. When you are looking to add a password manager to your Digital Life security plan, be sure to do just a little research to make sure you’re choosing well.
Like the cost of a VPN, the cost of using a password manager is multi-fold. There’s the recurring money cost to buy the service, the cost to educate yourself on how to use it, and the extra time it takes to use the service on a day-to-day basis. Again, this isn’t something trivial. I compare safely using the internet (and modern technology) to driving a car – we all had to go through some pretty significant training at the outset, and it took years of practice to get good at it. Even so, we all have accidents – nothing’s perfect. Using the internet safely takes a lot of training & education, which frankly most people neglect. This is why hacking is so profitable for the hackers!
Other actions (or inactions) that put you at risk include indiscriminate surfing, giving out personal information when you don’t have to, allowing online entities to collect information about you, and being lax about checking your privacy and security settings online and on your computer/device. I think you have an iPhone (and that’s part of the article’s thrust), so here’s some do’s and don’ts:
 If you have an iPhone, you should:
If you have an iPhone, you should:
- make sure that your email service provider is using SSL/TLS (see Settings > Accounts > and navigate to the Advanced section to make sure the SSL switch is on, as well as S/MIME).
- peruse the Settings > Privacy area and restrict privacy as much as you can. Go through each setting for every app you have installed on your iPhone.
- secure your iPhone with a passcode (4 digits is ok, more is marginally better) and fingerprints (I suggest at least one from each hand, and one from your husband/spouse/SO).
- make sure the iPhone is set to wipe itself if stolen (Settings > General > Touch ID & Passcode > Erase Data is switched on). That means that after 10 failed attempts, your iPhone is locked and securely wiped – a thief cannot get to your data, and they can’t even reset and use the iPhone in any other way.
- regularly prune unused apps by deleting them from your phone.
- when you install a new app, visit the settings in the app and/or in the Settings to make sure that you’ve restricted its use/access to your data prudently.
- surf the web responsibly, avoiding dodgy websites and avoid giving out your information online, by phone or in person
- treat with great suspicion all email messages, text messages, social media and other incoming information. Err on the side of paranoia rather than trust. Most security & technology warnings are fake.
Other smartphones (such as Android-powered smartphones) may require more security considerations.
A certain level of sacrifice of our privacy is inherent in using the internet, and the hacks getting in on the VPN bandwagon are capitalizing on the average consumer’s lack of understanding of the situation and unwillingness to educate themselves so they can make good choices. The truth is that your privacy has been sacrificed for well over a decade now, just about anything you’ve done online (email, websurfing, social media etc.) is already sitting in huge data stores. The best you can do is limit future compromises.
On the note of ‘free’ and absurdly low-cost services: in general, if you don’t pay for it, you are the product being sold.
I will be writing more in the coming weeks about VPN choices, once I’ve completed a comparative analysis.
This website runs on a patronage model. If you find my answers of value, please consider supporting me by sending any dollar amount via:
or by mailing a check/cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182. I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public. Thanks!







Pingback: NordVPN for iPhone - Practical Help for Your Digital Life®