Don’t be a Victim
How To Avoid Being A Victim Of Social Engineering

Social engineering is the intentional use of deceit to get information from individuals, which is then used for fraudulent purposes. In most cases, hackers find ways to lure unsuspecting culprits into giving them personal information that includes passwords for sensitive accounts such as bank accounts and emails addresses among other social sites. Internet users should know that it is never possible to be completely safe as long as they hold a social account. However, you can find ways to protect yourself from such activities. Take a look at some of the easiest ways you can achieve this.
Invest in a Strong Anti-Virus

While this product does not provide foolproof safety from attacks, it offers a certain level of security that Internet users appreciate. An antivirus ensures that malware, spyware, and other threats from hackers do not make it through to your system. They scan the Internet to see the intentions of each request you receive. Additionally, if you happen to download an untrustworthy document, the software will detect this and delete it before you can install it; thus, saving you a lot of heartaches that are connected to stolen information, which hackers use to demand a ransom from the victim.
Have Different Passwords

Most people have a single password that cuts across most if not all the social sites that they are members of. As such, hackers find it very easy to manipulate these individuals especially once they make such a discovery. To keep yourself safe from such instances, use different codes for each account. This way, anyone trying to breach the security of your social account will only succeed once. In addition to this, ensure that you change your passwords every so often.
Use Unique Passwords
Predictability is one of the leading causes of successful social engineering attempts. Most people use information that is easy to acquire such both theirs and their loved one’s dates of birth, anniversaries, names, and employment dates among others. What makes this a risky affair is the fact that such information is readily available to members of the public, especially if you are one who is fond of posting every detail about yourself on the Internet. You don’t have to use a password that looks like an app development code, but provides several variables when setting your security measures. Take care not to use characters that are naturally placed in chronological order. For example 123, ABC, asd, and qwe among others. While this may seem smart to you, remember there is someone out there who will decipher such information without making so much effort.
Virtual Private Networks to the Rescue
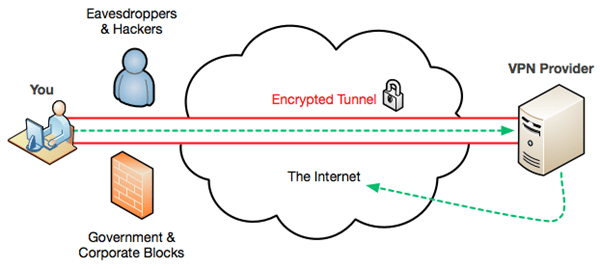
A virtual private network is a surfing option that allows you to browse with your identity and online transactions hidden. Consequently, you can browse the Internet from any location around the globe without the fear of compromising your security. VPN’s enable you to do a variety of online activities, which include surfing the Internet for leisure, moving funds using your online bank account, or performing any tasks related to your profession. If the nature of your activities on the Internet is not as heavy, you can opt to use free VPN’s. However, if the activities you conduct on the Internet may lead to a significant loss in the event of a security breach, buy a VPN from one of the providers online. Be sure to research thoroughly so you can know which virtual private network will work best for you before making any commitments.
Avoid Responding to Emails You Do Not Know

Criminals are known to use this tactic as bait. They pretend to be an organisation or company that is responding to an inquiry you made concerning a particular product or service. The minute you respond to such an email, they use the connection to send spyware and other malicious viruses. If you are not certain about the origin of an email, search the Internet to know whether it is legitimate or not. Also, go through your sent emails to see if you have a communication thread with the said sender before you choose to respond to them. Be slow to act even if the email sounds urgent.
Do Not Open Emails You Are Not Familiar With or Download Every File You Receive
Spammers are known to attach their spyware in emails or other attachments they send to you. If you are one to open emails you are not familiar with, this is how they take you down. Once you open the email or download the file, you leave yourself vulnerable to attacks considering that the virus will have gained an entry point. Even if the email is from a trusted friend or relative, check with them first considering that their account may have been hacked and is being used to gain information from all their contacts.
Put up Spam Filters

Although many people understand the need to set spam filters, not many take this step. Filters ensure that all unknown emails you receive are sent to the spam folder. As such, you do not have to deal with deleting such emails considering that you won’t see them. The shortcoming to this is that you may have to sift through this folder once in a while to see whether other important emails may have been clustered as spam. If you receive a complaint from one of your contacts concerning emails that you have not been responding to, check the spam folder.
Bottom Line
Social engineering is taking place rampantly all over the world. Individuals need to be very keen when it comes to giving information to people they are not familiar with, considering this is how every attack begins. If the email is not urgent to you, take time to see the demerits that may come with responding to it. Put up email filter options to the highest level possible to keep spammers at bay, and avoid clicking links that you receive in the email unless you have verified that they are safe. Antivirus can help do most of this work, but pair it up with a virtual private network just to be safe.
Kerry Harrison is a guest author from our friends at
https://www.vpngeeks.com
This website runs on a patronage model. If you find my answers of value, please consider supporting me by sending any dollar amount via:
or by mailing a check/cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182. I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public. Thanks!







