Windows 10 Ransomware Protection
Windows 10 Ransomware Protection: a reader asks…
I read your articles regularly, and am starting to get more worried about ransomware. I’m just a consumer with a computer running Windows 10. What should I do to protect myself?
Just a word of warning to all you consumers out there: The cybersecurity industry is seeing a lot more evidence of ‘commoditized ransomware use”. What this means is that those big, splashy ransomware attacks against big business are already coming to the small business and individual computer user world, and this is predicted to grow exponentially over the next year.
Ransomware packages are now a product line that can be purchased off the dark web for a quite reasonable cost. That means that smaller criminal groups and individual hackers can now deploy ransomware easily and cheaply. They’ve seen how lucrative the business can be, and their targets are going to be pretty much anybody – including you! So yes, now is the time to take steps to beef up your protection against ransomware.
Start with your computer – Windows 10 has ransomware protection built in. If you open your Windows Security app (click Start and type “Windows Security” and press your Enter key), go to the section “Virus and threat protection” on the left-side menu. At the bottom you will see a Ransomware protection listing. If it’s not turned on, turn it on, then click “Manage ransomware protection”.
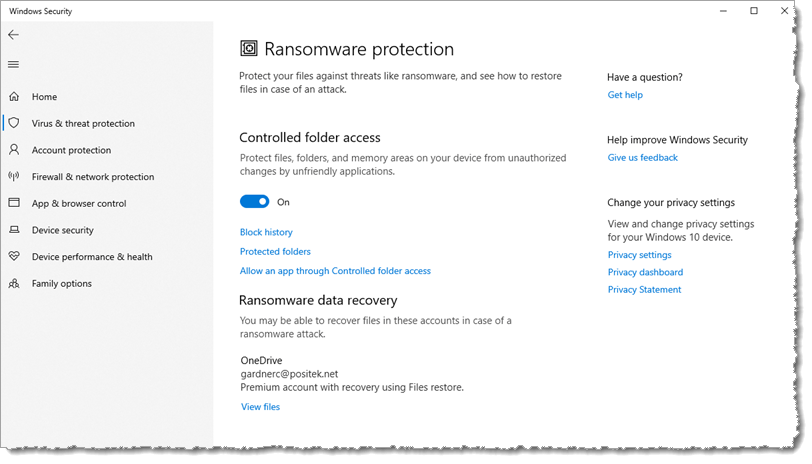
You’ll see a slider you should turn on, called “Controlled folder access”. This is not turned on by default, but almost everyone should turn it on. In a few cases, you might be using apps that will be affected by this setting. For that situation, there’s also a control to “Allow an app through Controlled folder access”. I’d suggest you wait till you find something you use that’s been blocked before you start using this utility – as it will tell you which apps have been blocked so you can easily add them. But don’t add apps nilly-willy – be sure it’s an app you need to use. Apps that provide visibility into your file system (3rd party apps, not the built-in File Explorer) will often be blocked.
That’s a good first step, but computer and online security is an iterative process, not a one-and-done action. You should be consistently following my safe computing guidelines, sprinkled throughout this website with some concentrated areas like my article Safe Digital Life. Recognize that the most common ways for a ransomware attack to begin is in an innocuous email, web page or popup window. Opening file attachments and clicking links without knowing what they (really) do) is a sure way to bypass your security and allow hackers access to your computer and digital life. Companies constantly try to educate their employees to prevent ransomware attacks, but the hackers seem to keep one step ahead. Evidence: the spate of successful ransomware attacks in the news every day.

We all need to take a more suspicious and, dare I say, paranoid approach to how you use your computer, the internet and even your phone. Every week I get calls and emails from scammers posing as somebody else, trying to get me to give them access to my digital life. Nobody, not the IRS, any business or government entity, or even someone you know should be asking for your login credentials to any online destination. Don’t give anyone your passwords or other online access credentials. For that matter, you should restrict all your personal information – don’t give out your birthdate, social security number, or other identifying information to anyone, even on social media. It’s just too risky these days.
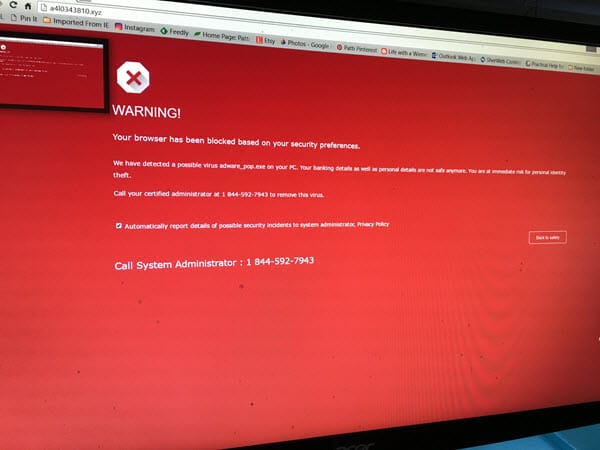
You may see one or more of the creative ways that hackers use to try to get you to fall for their scams. Email or phone messages may say they are confirming a purchase on Amazon or other business. Big and scary popups on your computer screen may warn you that your computer is infected and you must call a number to get your computer cleaned – sometimes even with audio! Don’t fall for these. If you’re at all unsure, here’s a handy tip:
Whip out your smartphone camera and take a picture of the screen, then send it to someone you trust who is computer savvy. Be sure to ask them what they think if it’s a scam or not. I can tell you, it’s always a scam.
The fake warnings are easy for hackers to fabricate, and they know that 1) at least some people will fall for them, and 2) they are an easy way to make money.
About that money aspect… Ransomware attacks don’t always mean a huge dollar ransom demand. As more individuals and small businesses get attacked, the hackers smartly set the dollar demands based on what they think they can realistically get from the victim. And even more scary, paying the ransom is no guarantee that the hacker will give you the means to unlock your personal files – hackers are by definition not bound by ethics or professionalism. They are simply motivated by money – getting as much as they can. As their business model matures, I’m sure we’ll see changes. But regardless, their business isn’t dependent on spreading by word of mouth or victim-instigated repeat business. So they will focus on extracting the most money they can from each and every interaction. Sadly, it’s “just business”.

If you’ve read this far, please, please take precautions to protect your digital life from scammers, hackers and ransomware. Make sure you have strong (long) and unique passwords for all your online accounts, keep your computers, tablets and smartphones updated (operating system and all installed apps/software), and read the news here and elsewhere to stay informed on the latest emerging threats. These hackers are smart and increasingly well-versed in using psychology to get us to do something unsafe. Don’t be an easy victim.

One last note, I’m sure you’ve read about the primary answer to avoid having to pay ransom to get your files back. That involves backing up all your personal files on a regular basis, and keeping that backup offline when you’re not actively backing up. The easiest way to do this is for most consumers is to use an external hard drive (such as the popular Western Digital My Passport drives, such as this 1tb model at Amazon). This drive requires no separate electrical power (runs off USB power). Simply connect it to your Windows 10 computer and turn on File History (Start>Settings>Update & Security>Backup>Add a drive) to automatically backup all your personal files to that drive. Leave it plugged in for a day or so, so it can create a full backup. Then unplug it. Don’t forget to plug it in as often as you wish for a few hours so it’ll get all the changed and new files you’ve worked with since the last time you plugged it in. Then, unplug it again till the next time.
You can perform that little procedure to backup as often as you wish, once a day, once a week, or less often. If you fall victim to a ransomware attack, you can simply wipe the computer, re-install Windows 10 and all your programs, then plug in that hard drive and restore the files (Start>Settings>Update & Security>Backup>More options>Restore files from a current backup).
This website runs on a patronage model. If you find my answers of value, please consider supporting me by sending any dollar amount via:
or by mailing a check/cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182. I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public. Thanks!








Hi Chris, thanks for another helpful article. I’ve been running Malwarebytes software for some time and it also has a ransomware protection feature, which I have turned on. With the built in Microsoft Security software, it looks like real time scanning can not be enabled with another virus protection software running, so it is just set to do periodic scans. Without real time scanning enabled, it looks like the controlled folder access feature you mention can’t be activated. So is there a gap in my protection?
Hi Michael, thanks for your comment. Actually Malwarebytes Premium works well alongside Microsoft Defender. This is the only pairing I would consider. The trick to make it work right is to go into the Malwarebytes settings and turn off registering it in the Windows Security Center. Then both can run full-time protection.
Great article and advice, but one question: I’ve been using Malwarebytes virus and ransomware protection and wonder if it is comparable to Windows File Protection. They can’t be both used at the same time.
Hi Ed, thanks for your comment. Actually, you can run both of them. As in my reply to Michael’s comment, you have to uncheck a Malwarebytes setting to register it in the Windows Security Center (e.g., not registering Malwarebytes) so that both will run full time. I have been doing this for over two years without any problems. Malwarebytes Premium is the only third-party security program I’d recommend running along with Microsoft Defender. All the others I’ve tried won’t work well-they take too many resources, and slow down the computer significantly. And, they take a lot of finagling to avoid disabling Microsoft Defender. With Malwarebytes, it’s only that one setting change.
It is NOT necessary to include in the backup cloud files that are sync’d to my local drive, correct? Such as one drive files that are sync’d to my local computer. Since those are already saved on the cloud (and others such as amazon drive; box.com; dropbox,) I can always resync if my computer crashes or get hacked, correct?
Hi Mike, yes, as long as files are in more than one place and one of those places is “offline” you should be fine. The absolute best backup is one that’s only connected when you’re actually backing up, not connected full-time. If a backup drive (NAS or cloud) is connected when the ransomware attack happens, there’s a chance that other drive could also be encrypted when it syncs the local file(s) with the NAS/cloud file storage space. It depends on the sophistication of the attack and how you have configured that drive to work on your computer.
Generally, if Windows’ File Explorer or macOS’ Finder can easily get to a drive, it can be encrypted. If another step is needed (like entering in a password or 2-factor code) the ransomware can’t get to it, so it’s protected.
Some cloud-based file storage services have non-destructive synchronization (aka “versioning”), so that if you delete or encrypt a file or folder locally, the cloud version can be restored back one or several versions. If your cloud-based file storage service doesn’t do that, then encrypting a local file results in an encrypted cloud copy. That’s worth checking out with your service provider.
I think Dropbox, OneDrive, Google Drive, Amazon Drive and iCloud Drive have this feature built-in, but it either might not be activated, or is a ‘premium’ feature not available without a fee. You should definitely check out your service provider’s terms and settings. I should note that Microsoft OneDrive does have automatic 30-day versioning, but it is a file-by-file method of recovery. That can make for a really time-intensive recovery process, should you suffer a successful ransomware attack.
For anyone who wants to make sure to have the best protection against ransomware, and to have a quick restoral/recovery process, I still recommend an offline storage medium that’s only connected when you perform a backup of your files and then disconnect it in-between backups.