Your Processor Leaks

Your Processor Leaks: a reader asks…
I just read about the security bug in Intel processors. Can you give me a quick rundown on what’s going on and what I should do about it?
The start of 2018 brought us a new computer security worry. Google’s Project Zero team (and teams at Graz University and Cyberus Technology) discovered a huge security vulnerability with virtually all Intel (and probably AMD and ARM) processors. The vulnerabilities are called “Meltdown” and “Spectre” (there are several variants of Spectre). What this means is that hackers could potentially gain access to sensitive information that should be locked up tight in the processor. Hackers could potentially see your personal data that the processor (CPU) makes available outside of itself, at least temporarily.
This is a serious issue affecting almost every computer on the planet. Depending on your operating system, you may need to take some action. Linux users were given a patch on Jan. 1st 2018 that provided a software workaround to patch the vulnerability. Microsoft did the same thing on Jan. 3rd. Apple says that the latest version of MacOS (High Sierra, MacOS 10.13.2) is already protected.
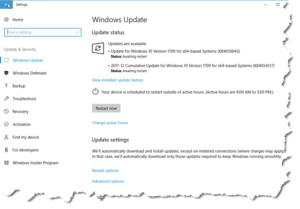 For Windows users, you should run Windows Update and install any updates it reveals. In particular, KB4056892 is the update patch that was released on Jan. 3rd. Since tens of millions of consumers are trying to do the same thing as you, you may not see this update appear for several days, but keep trying until you get the update. You’ll need to restart your computer when the update has finished installing, and this update may add an extra few minutes to that first restart to finish installing itself into Windows 10. Oh, and there are reports that this update will slow your computer down a bit – but that’s just the cost of being secure. I have installed this update on several Windows 10 computers and haven’t noticed any significant difference. My recommendation is do not delay and install KB4056892 as soon as possible.
For Windows users, you should run Windows Update and install any updates it reveals. In particular, KB4056892 is the update patch that was released on Jan. 3rd. Since tens of millions of consumers are trying to do the same thing as you, you may not see this update appear for several days, but keep trying until you get the update. You’ll need to restart your computer when the update has finished installing, and this update may add an extra few minutes to that first restart to finish installing itself into Windows 10. Oh, and there are reports that this update will slow your computer down a bit – but that’s just the cost of being secure. I have installed this update on several Windows 10 computers and haven’t noticed any significant difference. My recommendation is do not delay and install KB4056892 as soon as possible.
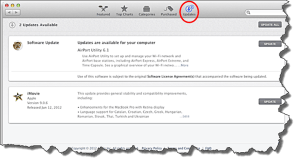 For Apple Mac users, if you don’t already have MacOS 10.13.2 installed, then open the App Store and go to the Updates tab and install it. If you don’t already have High Sierra installed, then now’s a good time to upgrade (it’s free). From the App Store’s main page, click the High Sierra upgrade link. Apple says that the 10.13.2 update won’t slow your system down any. I’ve installed this on my Macbook and don’t notice any system performance issues.
For Apple Mac users, if you don’t already have MacOS 10.13.2 installed, then open the App Store and go to the Updates tab and install it. If you don’t already have High Sierra installed, then now’s a good time to upgrade (it’s free). From the App Store’s main page, click the High Sierra upgrade link. Apple says that the 10.13.2 update won’t slow your system down any. I’ve installed this on my Macbook and don’t notice any system performance issues.
For you system administrators out there, be aware that this security vulnerability also affects servers. You should already have an update process in place and are following that plan. Since all webservers also run on affected processors, every website hosting company should be taking swift action to patch their servers so your website can’t be compromised by this issue.
Additionally, there’s the potential that this security vulnerability also affects smartphones and tablets, streaming video devices and perhaps some IoT devices. The only advice I can give you is to apply any system and firmware updates as soon as they are released. If your device doesn’t already have an update utility built-in, visit the manufacturer’s website and search for updates for your device. I suggest you don’t delay because it’s only a matter of time before hackers figure out how to exploit this vulnerability and deploy malware and other attack vectors across the internet.
Update: Mozilla has confirmed that these vulnerabilities can be exploited through your web browser (not just Firefox either), so be sure that you have updated to the latest version of your web browser, and that you are using a separate password manager (like LastPass or 1Password) instead of the password and autofill features built into your web browser. This applies across all web browsers including: Edge, Chrome, Firefox, Safari, Opera and the new Vivaldi.
2nd Update: This issue is rapidly developing, so lots of information and advice may change over the next few days. At this point, if your Windows 10 computer has a 3rd party antivirus product installed (instead of using the built-in Windows Defender), then the patch may not be enabled. It’s up to your 3rd party vendor to make sure their software implements a patch for the vulnerability, which may require a version update. This doesn’t mean you shouldn’t install the Windows Update patch, just that it may not actually do anything until your 3rd party vendor does their job.
This website runs on a patronage model. If you find my answers of value, please consider supporting me by sending any dollar amount via:
or by mailing a check/cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182. I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public. Thanks!
 Update: Mozilla has confirmed that these vulnerabilities can be exploited through your web browser (not just Firefox either), so be sure that you have updated to the latest version of your web browser, and that you are using a separate password manager (like
Update: Mozilla has confirmed that these vulnerabilities can be exploited through your web browser (not just Firefox either), so be sure that you have updated to the latest version of your web browser, and that you are using a separate password manager (like 






Pingback: Browser Search Change - Practical Help for Your Digital Life®
Pingback: Spectre & Meltdown Updates - Practical Help for Your Digital Life®