2-factor spoofing
 2-factor spoofing: a reader asks…
2-factor spoofing: a reader asks…
I hear you about using 2-factor authentication and have been looking at the online places I visit to see if they offer it. I just turned it on for my gmail account. But someone told me that hackers are able to defeat this security method, so I’m wondering if the extra hassle is worth it?
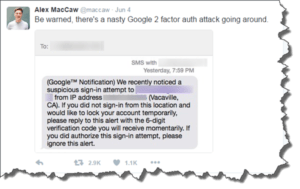
In a word, yes, it’s worth it. What your friend was probably referring to was a tweet put out by Alex MacCaw, cofounder of data API company Clearbit. It showed a social engineering hack attempt to get past the 2-factor authentication. This isn’t a direct attack on 2-factor authentication, but an attempt to fool a person into compromising the security feature. If you receive such a text message, you should ignore it, or any attempts to get you to send any authentication information (a code, passcode or password) to anyone, by text, email, phone or any other method. The six-digit code that you get via text message when Google or any other entity sends you should only be input into that online entity’s webpage. Once used, it’s now useless to anyone else because it’s a one-time use code.
 Hackers are constantly dreaming up new and creative ways to circumvent your digital security. Here are just a few examples I’ve run across lately:
Hackers are constantly dreaming up new and creative ways to circumvent your digital security. Here are just a few examples I’ve run across lately:
- A caller says he’s from Microsoft tech support and tells you your computer is infected and Microsoft servers have detected it. He’ll ask for remote access to your computer so he can ‘fix it’, but what really happens is that he infects your computer and compromises everything on it – and everything you do with it in the future.
- An email comes from your bank or credit card institution with a link to login and verify your account details. The link takes you to a fake website that looks like the real one, and when you login, your account is now compromised.
- A text message comes in saying your account is at risk and telling you to do something. Such text messages are always a scam.
- You get a physical letter in the mail that looks official, telling you to do something to protect your identity or verify your account. In almost every case, it’s fake.
- You get an email saying you have a Fedex or UPS package waiting to be delivered, and with a file attachment of your receipt. The email attachment actually infects your computer and compromises your digital life.
- You get a phone call or email or text from a ‘friend’ who’s stuck overseas and needs you to wire them some money so they can get home. The money goes to a scammer, your friend was never involved.
The list could go on and on. Scams are so prevalent that most people take a paranoid perspective to every communication they receive. Email is particularly suspect, since it’s so easy to fake an email’s From line and content. Text messages are so popular now that hackers and scammers have started targeting consumers through texting. So we all need to be more careful, and more suspicious of any incoming communications.
 In the case of the text scam you mentioned, someone attempting to get into your gmail/google account would have to already have your password. That’s not as remote a possibility as you think, millions of user credentials have been compromised over the last few years, and it’s quite possible that your password is among them. With 2-factor turned on, the scammer sends you that text message, and then attempts to access your google account. You then get a text message from google with the six-digit code, which the scammer hopes you’ll copy into a reply to their text (which is from a different thread). If you do that, they have about a minute to enter that code into google and gain access to your account. Then they’d immediately make changes such as changing the password, turning off 2-factor authentication, changing the phone number for your google account, etc. They also have access to your google account to look at your email, send email as if they were you, and use it to gain access to your other online accounts. For instance, banking – they’d visit your bank and use your email address and the forgotten password feature to reset the password.
In the case of the text scam you mentioned, someone attempting to get into your gmail/google account would have to already have your password. That’s not as remote a possibility as you think, millions of user credentials have been compromised over the last few years, and it’s quite possible that your password is among them. With 2-factor turned on, the scammer sends you that text message, and then attempts to access your google account. You then get a text message from google with the six-digit code, which the scammer hopes you’ll copy into a reply to their text (which is from a different thread). If you do that, they have about a minute to enter that code into google and gain access to your account. Then they’d immediately make changes such as changing the password, turning off 2-factor authentication, changing the phone number for your google account, etc. They also have access to your google account to look at your email, send email as if they were you, and use it to gain access to your other online accounts. For instance, banking – they’d visit your bank and use your email address and the forgotten password feature to reset the password.
Don’t fall for these scams, the weakness of our digital lives is more often ourselves, rather than the technology itself. Social engineering is the art of getting you to do something – tricking you into compromising your security and subsequently, your digital life. Do use 2-factor authentication everywhere you can, do use a password manager so you have strong, long, unique and un-guessable passwords on every online destination, and do practice good security in all your dealings with technology. I have a handy guide in my article: Safe Computing Practices.
This website runs on a patronage model. If you find my answers of value, please consider supporting me by sending any dollar amount via:
or by mailing a check/cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182. I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public. Thanks!







