Don’t get Phished
 Don’t get Phished: A reader asks…
Don’t get Phished: A reader asks…
Hi Chris, I’m hearing more and more about ‘phishing‘ and my company has even setup mandatory training for all employees. Before I go to that training, can you give me a quick primer on what it is and what to watch out for? I’m not sure why we are worrying about this, we’re just a small company.
More and more companies are coming to the realization that if they hold sensitive information on their servers, they are potentially liable for data breaches, particularly if they haven’t trained their employees in basic computer security. More and more victims are suing companies that hold their data when those companies get hacked. More of those suits are resulting in damages paid to the victims because the companies didn’t take all prudent steps to protect the customer data. And small business doesn’t get a pass on cybersecurity liability – hackers have discovered that small business is an attractive target since many small companies haven’t done anything about cybersecurity and are easy to hack. Cybersecurity insurance companies are seeing a lot more data breaches from companies that do under $2 million worth of business.
One of the easiest-to-exploit vulnerabilities of any company is its employees. Just about everyone has to use technology in their jobs these days, and the opportunities that hackers employ take advantage of human…frailties…particularly in regard to cybersecurity. We are a trusting bunch, and are easy to fool – that’s what phishing is.
Phishing is the attempt to acquire sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money), often for malicious reasons, by masquerading as a trustworthy entity in an electronic communication.
 While phishing attempts are mostly depicted as fake emails, I would expand that further – any communication method (telephone and person-to-person) can and is being used to ‘phish’ sensitive information. At least once a month I get a phone call from someone (usually with a foreign-sounding accent) saying they’re ‘from Microsoft’ and that my computer is infected. They follow-up with a request to remotely connect and ‘clean’ my computer. Absolutely bogus, if anyone allows someone they don’t know remote access to their computer, they are just asking for every bit of data to be stolen. Another example is someone calling in to request information on ‘their own account’. Impersonating a client is easy to do, since we are more likely to trust someone we’re talking to.
While phishing attempts are mostly depicted as fake emails, I would expand that further – any communication method (telephone and person-to-person) can and is being used to ‘phish’ sensitive information. At least once a month I get a phone call from someone (usually with a foreign-sounding accent) saying they’re ‘from Microsoft’ and that my computer is infected. They follow-up with a request to remotely connect and ‘clean’ my computer. Absolutely bogus, if anyone allows someone they don’t know remote access to their computer, they are just asking for every bit of data to be stolen. Another example is someone calling in to request information on ‘their own account’. Impersonating a client is easy to do, since we are more likely to trust someone we’re talking to.
But classic phishing often involves an email that you receive. It appears to be legit, usually has either a file attachment for you to open or a link to click. For the most part, you should never open an email file attachment, especially a zip file. For hyperlinks in an email, you should at the least hover over the link and read the popup URL to make sure it’s going to a legitimate website. I go into more detail about phishing emails in my article from last year. So here’s my quick hit-list of things to watch out for in phishing emails:
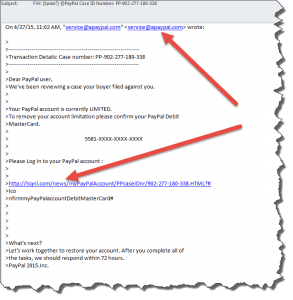
 The From address words don’t match the domain name (such as Chase Bank Services and cbs@gmail . com) – the domain name (the part after the @ sign in email addresses should always match an independently verified search of the company or entity. Another example: papal.com is not Paypal.com
The From address words don’t match the domain name (such as Chase Bank Services and cbs@gmail . com) – the domain name (the part after the @ sign in email addresses should always match an independently verified search of the company or entity. Another example: papal.com is not Paypal.com- The subject line has spelling or grammatical errors – it if looks like it was written by someone not fully fluent in your language, then it’s more likely to be coming from a scammer
- File attachments – unless you are expecting an email with a file attachment from someone you know, you have no business opening email file attachments. This has been the most common method used to distribute malware and computer viruses since the internet was born. In particular, don’t open file attachments that end in .zip, .exe, .com or .bat. But really, don’t be an easy mark – don’t open any file attachments.
- Hyperlinks that don’t match what they say. It’s absurdly easy to fake a hyperlink. Such as this link: www.google.com which actually goes to www.yahoo.com (and that one goes to www.google.com). Before you click on any hyperlink in an email, hover over it and read the address (shown in a popup tooltip or at the bottom-left of your browser window) – make sure it goes to the company it says.
- Hyperlinks that take you to a different website than you expect – similar to above, the hyperlink may say something innocuous like “your bank security department” and if you’re naive enough to click on the link, the website that opens isn’t your bank’s. Check the URL and make sure the web address is real. For example, https://positek.net is the real address of my website, but https ://www.positek.net.fake.com isn’t. After the http:// (or https://) there should be a string of domain name and suffix (.com, .net, .org, etc.) and the only thing after that (if anything) should be a slash and something else. Adding more domain name information before the final .com (.net, .org, etc.) really takes you to a different domain than anything that comes in front of it.
http:// www.domainname.com takes you to to the domain “domainname”
http:// www.domainname.faker.com takes you to the domain “faker”
http:// www.domainname.com.faker.com takes you to the domain “faker”
- Warnings – all types, including warnings about phishing. Let’s face it, in the 21st century email is the last place you’ll trust when it comes to warnings about anything. Your bank, credit card company, internet service provider all know how unsafe email is, and won’t use that for anything other than marketing. If they do, perhaps it’s time to find a smarter bank…
- Log in requests – if the website is asking you to click a link and log into your account, there’s a good chance it’s a phishing attempt.
Below the fold
More and more small companies are getting cybersecurity insurance (which is an outgrowth of professional liability insurance) to deal with the increased threat from hackers. Insuring companies are learning quickly that a company that holds sensitive data but doesn’t take steps to make sure employees know how to protect that data doesn’t have a valid claim – insurance doesn’t cover negligence. From the company’s perspective, negligence means they didn’t train their employees in the basic tenets of cybersecurity. Some companies didn’t even have a disaster recovery plan for their customer data. Claims for recompense after a data breach are coming under increasing scrutiny by the insurance companies and it’s becoming a nightmare for small businesses to navigate as they often lack enough funding for adequate training.
This website runs on a patronage model. If you find my answers of value, please consider supporting me by sending any dollar amount via
 (send to @PosiTek),
(send to @PosiTek),  (send to Support@PosiTek.net),
(send to Support@PosiTek.net),  using any credit card (no Paypal account required), using Zelle, Apple Pay or Google Pay, or by mailing a check or cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182.
I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public.
Thank you!
using any credit card (no Paypal account required), using Zelle, Apple Pay or Google Pay, or by mailing a check or cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182.
I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public.
Thank you!
 The From address words don’t match the domain name (such as Chase Bank Services and cbs@gmail . com) – the domain name (the part after the @ sign in email addresses should always match an independently verified search of the company or entity. Another example: papal.com is not Paypal.com
The From address words don’t match the domain name (such as Chase Bank Services and cbs@gmail . com) – the domain name (the part after the @ sign in email addresses should always match an independently verified search of the company or entity. Another example: papal.com is not Paypal.com



