Fake Email Voicemail
 Fake Email Voicemail: a reader asks…
Fake Email Voicemail: a reader asks…
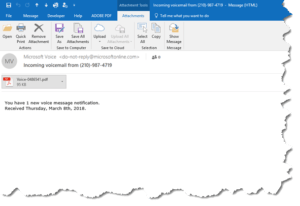
I received a strange email from Microsoft with an attached pdf. What should I do with this?
Don’t open the file attachment. Do not pass go, do not collect malware on your computer (sic). This is a phishing attempt to get you to compromise your computer security. Nefarious hackers are very creative in the ways they’ll attempt to get you to bypass any security you’ve added to your computer. Based on your screenshot, you received an email in Outlook (on a Windows 10 computer ostensibly), coming from a microsoftonline.com address.
Since you forwarded the email to me (as an attachment) I could examine it more thoroughly than if you’d only sent a screenshot (or used the standard ‘forward’ feature of Outlook). By forwarding the email as an attachment, I get the email complete with the hidden headers and the attached file intact. Examining the headers reveals that the email didn’t actually come from Microsoft. You can do this with the email open in Outlook by clicking File > Properties. That gives you a lot of transmission detail on exactly where the email came from and lots more. Deciphering that mess of information showed that the email in fact came from a different email address (the “X-Sender”) which in itself is probably a fake email address as well. The email came from an IP address in New York, which could easily be some hapless person’s personal computer (that was hacked).
 Taking a look at the attachment (which you shouldn’t do), it is an Adobe PDF that simply has a link to click to supposedly listen to a secure voicemail message from Office 365. Hovering over the link shows that if clicked, it will open your web browser to a website that is almost certainly infected with malware and would probably infect your computer.
Taking a look at the attachment (which you shouldn’t do), it is an Adobe PDF that simply has a link to click to supposedly listen to a secure voicemail message from Office 365. Hovering over the link shows that if clicked, it will open your web browser to a website that is almost certainly infected with malware and would probably infect your computer.
You should make it a practice to never open email file attachments unless you are 100% sure they are safe. Since email is so easy for anyone to fake, that really means almost never. Anyone can easily configure their email program to send mail as if they were someone else, and anyone can easily create a hyperlink that says one thing but actually does another. Hyperlinks are absurdly easy to fake, for example:
- Here’s a link: https://positek.net but if clicked will actually open a google search page
- Here’s a link: https://google.com but if clicked will actually open my website home page
Of course, I crafted innocuous fake hyperlinks above, while hackers are going to craft sneaky hyperlinks that will take you to unsafe places. I hope that everyone treats email (especially file attachments but also any hyperlinks in emails) with suspicion bordering on paranoia. Never assume something is safe to click or open. Your safest course of action is to simply delete the email in question. If you get other emails that are suspicious-looking in any way, err on the side of safety and delete them unread.
This website runs on a patronage model. If you find my answers of value, please consider supporting me by sending any dollar amount via:
or by mailing a check/cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182. I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public. Thanks!








thanks for sharing a post.