Scam Email Word Doc
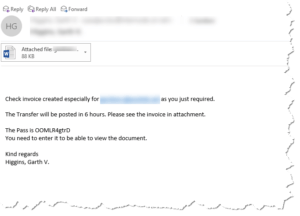 Scam Email Word Doc: a reader asks…
Scam Email Word Doc: a reader asks…
I recently received an email from someone I don’t know who sent me a Word document for something he says I asked for. I’m not sure what to do. I have Outlook and saw the note in my preview window but haven’t opened the email yet. What should I do?
Do not pass Go, delete the email without opening it or the file attachment. Scammers and hackers are constantly finding new and creative ways to get past your defenses and infect your computer. It’s almost certain that the attached Microsoft Word document has an infected macro in it that would do nasty things to your computer if you allow it. No matter what other protections (antivirus, anti-malware, etc.) you have, Word macros can bypass them all and cause mayhem. For instance, the Locky ransomware malware is now being passed around embedded in Word document macros. If you allow that macro to run, Locky would encrypt your entire hard drive and offer to ‘sell’ you a key to unencrypt it.
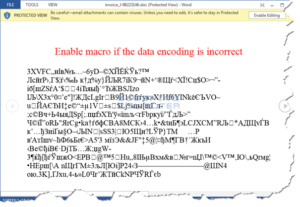 Don’t fall for this scam. If you were to open the Word document you might see a message telling you to enable macros on the document – doing so would unleash a potential infection that could turn your computer into a paperweight. You should treat all unsolicited incoming communications with great suspicion. That includes email, text messages, social media, phone calls, physical letters in your mailbox and even unsavory characters knocking on your door. Bad people are working very hard to scam you.
Don’t fall for this scam. If you were to open the Word document you might see a message telling you to enable macros on the document – doing so would unleash a potential infection that could turn your computer into a paperweight. You should treat all unsolicited incoming communications with great suspicion. That includes email, text messages, social media, phone calls, physical letters in your mailbox and even unsavory characters knocking on your door. Bad people are working very hard to scam you.
When it comes to email, it doesn’t even matter if the email looks official or looks like it comes from someone you know. Email is absurdly easy to fake, and is the most common way that scammers and hackers use to bypass your computer protections. That’s because they depend on our natural tendency to trust, and if we unknowingly or unthinkingly give permission for malware to infect our computers, we are bypassing our protection programs. Protection programs (like Bitdefender & Malwarebytes) are good at telling us we’re doing something risky, but if we ignore the warnings, they can’t protect us from ourselves.
This website runs on a patronage model. If you find my answers of value, please consider supporting me by sending any dollar amount via:
or by mailing a check/cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182. I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public. Thanks!







