Spectre & Meltdown Updates

Spectre & Meltdown Updates: a reader asks…
I’ve been reading about two serious-sounding hardware vulnerabilities, Spectre and Meltdown. Just the other day I read about Microsoft issuing a new patch that undoes the patch they issued on January 3rd. What gives, and what should I do?
It’s an understatement to say this situation is all fouled up. I last wrote about this on January 3rd in my article Your Processor Leaks, so consider this an update to that. Intel ‘fessed up to the fact that the mitigation they’d released (in firmware for the Central Processing Unit – CPU) was, shall we say, half-baked and might cause problems with some computers. So the patch that Microsoft released on January 3rd needed to be rescinded in some way. On Saturday, January 27, Microsoft released another patch on Windows Update to do so, but that patch may take awhile to get installed on your computer. You can check Windows Update’s history and look for these:
- An update installed on or after January 3rd that references KB4056892 – this is the original patch for the vulnerabilities that Microsoft released after Intel issued their own patch.
- An update installed on or after January 27th that references KB4078130 – this is the patch that reverses the January 3rd patch’s effects.
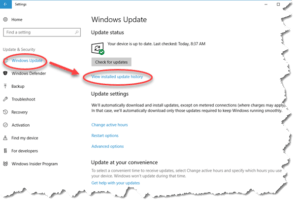 To see your Windows Update history, click your Windows 10 start button (bottom-left of your screen, the four white window panes), then click the gear icon. That opens a new window with a menu down the left side. Click on the Windows Update menu item. On the resulting window, click the ‘View Installed Update History” link.
To see your Windows Update history, click your Windows 10 start button (bottom-left of your screen, the four white window panes), then click the gear icon. That opens a new window with a menu down the left side. Click on the Windows Update menu item. On the resulting window, click the ‘View Installed Update History” link.
At this point, I think most consumers should do the following:
- Defer installing any BIOS or firmware updates from your computer manufacturer at this time, until everybody is confident that the updates will solve the vulnerability without seriously compromising reliability and performance on their computer.
- Leave Windows Update on automatic updates, and restart your computer more often than usual. I suggest once every other day or so. This restart will simply help keep buggy code cleared out of memory, it won’t do a thing to give you better or more protection against the threats.
- Be very paranoid about how you use the internet – take my safe computing practices to heart. Avoid installing anything on your computer unless you are 100% sure that it’s safe. Surf responsibly and avoid dodgy websites. Don’t click on links or open attached files in email unless you’re sure they’re safe. Don’t trust anyone to give you good advice who hasn’t already proven themselves to be trustworthy.
If you don’t want to wait for Windows Update to give you the “Saturday special” patch, you can get it here (note that this is not for 64-bit Windows operating systems). I will continue to update this article as things develop.
This website runs on a patronage model. If you find my answers of value, please consider supporting me by sending any dollar amount via:
or by mailing a check/cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182. I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public. Thanks!







Pingback: Windows 10 Power Options - Practical Help for Your Digital Life®
Pingback: Lenovo Critical Updates - Practical Help for Your Digital Life®