Ransom32 – Mac, Win & Linux
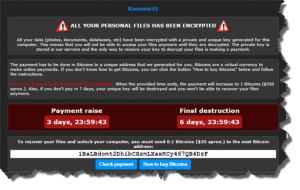 Ransom32 – Mac, Win & Linux: A new version of ransomware has popped up, and this hacker tool threatens not just Microsoft Windows computers, but also Mac and Linux computers. The bad actors who created this monster made it in Javascript so it’s out there affecting Windows computer users right now. It’s quite possible that the program has been or will be re-formulated into versions that will run on Mac and Linux as well.
Ransom32 – Mac, Win & Linux: A new version of ransomware has popped up, and this hacker tool threatens not just Microsoft Windows computers, but also Mac and Linux computers. The bad actors who created this monster made it in Javascript so it’s out there affecting Windows computer users right now. It’s quite possible that the program has been or will be re-formulated into versions that will run on Mac and Linux as well.
I wrote about this last November in this article, and introduced ransomware in this article. For a detailed outline of what is ransomware, check out my article What is Ransomware. This threat is growing quickly as a major attack on consumers everywhere, since it’s easy to construct and has a great (for the hackers) payoff. Your only good solution is to avoid infection. If your computer becomes locked up by ransomware you really have only two options:
- Wipe the computer and reinstall Windows and all your programs from scratch (or just buy a new computer), and restore a good backup of your personal files, or
- Pay the ransom and hope that the perpetrator doesn’t stiff you.
 Because ransomware encrypts your files with a hidden key, there’s really no way you can get them unencrypted without the ‘key’. And the perpetrator will most likely use Bitcoin, an untraceable payment method, so you can’t track them down. Even paying the ransom may not get you a workable key to decrypt your files, you are completely at the mercy of the hacker.
Because ransomware encrypts your files with a hidden key, there’s really no way you can get them unencrypted without the ‘key’. And the perpetrator will most likely use Bitcoin, an untraceable payment method, so you can’t track them down. Even paying the ransom may not get you a workable key to decrypt your files, you are completely at the mercy of the hacker.
If you’ve neglected to keep a backup of your personal files someplace other than your computer, then you are simply out of luck getting them back unless you pay the ransom and the hacker gives you a working key. So at the very least, everyone should be putting a computer backup on the top of their to-do list asap. So what’s involved in avoiding being infected? Using your computer safely. I’ve laid out a bunch of safe computing practices in this article, but let me lay out the three most important tasks, focused on avoiding being infected with ransomware. My advice here isn’t just for computer experts, but for the average computer user:

First, have good protection programs installed on your computer. For Windows this is critical, and I recommend a layered defense set: Bitdefender Internet Security, Malwarebytes Anti-Malware Premium, and Malwarebytes Anti-Exploit Premium. If you already have an antivirus program you can skip Bitdefender and just get the two Malwarebytes programs.
For Macs, it’s time to get yourself some protection. Again, a layered defense is best, and I recommend ClamXav, or Malwarebytes Anti-Malware for Mac. If you think this advice is wrong, you should take a look at The Mac Malware Guide, by Thomas Reed at The Safe Mac, who I trust and who stands behind the Malwarebytes product.
 Second, get yourself an external hard drive or a thumbdrive (if you only have a few personal files) and backup all your personal files on a regular basis. We have an easy procedure at the bottom of this article. An alternative is to put all your personal files in the cloud – Dropbox, Google Drive, Amazon Cloud Drive, iCloud Drive, Microsoft One Drive are all options.
Second, get yourself an external hard drive or a thumbdrive (if you only have a few personal files) and backup all your personal files on a regular basis. We have an easy procedure at the bottom of this article. An alternative is to put all your personal files in the cloud – Dropbox, Google Drive, Amazon Cloud Drive, iCloud Drive, Microsoft One Drive are all options.
Third, take a paranoid approach to every email you open, every webpage you look at, and anything you click on. Don’t click on something to see what it is or does, or try out free programs you can download from the internet. Tamp down that curiosity itch – the hackers are depending on it to proliferate.
For email, you should never open a file attachment in an email directly. Your best bet is to save the attachment to your computer and then scan it with your protection programs to make sure it’s safe before you open it. This includes file attachments sent from people you know – you have no idea if their computer is infected or not.
When viewing webpages, avoid clicking on anything you don’t know is safe. In particular, don’t download, install, or run any program on your computer without checking first to make sure it’s safe. Many programs that you can get for free on the internet are laced with malware, and if laced with ransomware, you’re computer becomes as useful as a paperweight.
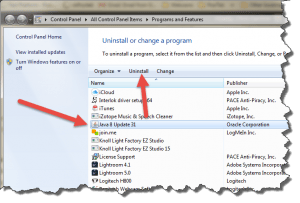 Fourth, it’s time to remove Java (but not JavaScript) and Adobe Flash from your computer, along with any other program or feature you don’t use and/or need. After email file attachments, Java and Flash have become two of the most common ways for hackers to infect your computer. While JavaScript is the way Ransom32 was created, you still need that program (built into your web browser) in order to do most anything on the internet these days. But websites are moving away from Adobe Flash for displaying video, favoring HTML5, and most websites don’t use or need Java at all, so you may not even miss these. To uninstall programs from your computer, click Start and type ‘uninstall a program’ and press your Enter key. Go down the list of installed programs and select each one in turn that you don’t need, then click the Uninstall link above the list and follow the on-screen instructions. For Macs, use these instructions to remove Java, and these instructions to remove Flash. Most other programs on a Mac can be removed by simply trashing the program from your Finder’s Applications folder.
Fourth, it’s time to remove Java (but not JavaScript) and Adobe Flash from your computer, along with any other program or feature you don’t use and/or need. After email file attachments, Java and Flash have become two of the most common ways for hackers to infect your computer. While JavaScript is the way Ransom32 was created, you still need that program (built into your web browser) in order to do most anything on the internet these days. But websites are moving away from Adobe Flash for displaying video, favoring HTML5, and most websites don’t use or need Java at all, so you may not even miss these. To uninstall programs from your computer, click Start and type ‘uninstall a program’ and press your Enter key. Go down the list of installed programs and select each one in turn that you don’t need, then click the Uninstall link above the list and follow the on-screen instructions. For Macs, use these instructions to remove Java, and these instructions to remove Flash. Most other programs on a Mac can be removed by simply trashing the program from your Finder’s Applications folder.
Be brutal and get rid of as many programs as you can. This makes your computer leaner and less complicated, which translates to faster and more reliable. If something does go wrong, it’s much easier to diagnose and fix if you don’t have dozens of programs mucking up the situation. Keeping it simple isn’t stupid, it’s smart when it comes to our computers (and really, most any consumer technology).
I get that the third and fourth items above are not as easy and do-able as the first two. My hope is that the first item will catch ransomware before it infects your computer, and the second gives you a way to recover without losing everything, should ransomware get by your protection programs. There is no sure thing, and that’s why items #3 & #4 are important as well.
This website runs on a patronage model. If you find my answers of value, please consider supporting me by sending any dollar amount via:
or by mailing a check/cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182. I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public. Thanks!







