Watch out for “Ransomware” apps – Updated
 This danger appears to be spreading quickly since September 2013. Latest info in: they’ve extorted over $5M US from people since the ransomware craze started last fall. A member asks…
This danger appears to be spreading quickly since September 2013. Latest info in: they’ve extorted over $5M US from people since the ransomware craze started last fall. A member asks…
I saw a pop-up that appeared on my computer warning me that I needed to buy their app to make sure my computer is safe. What should I do?
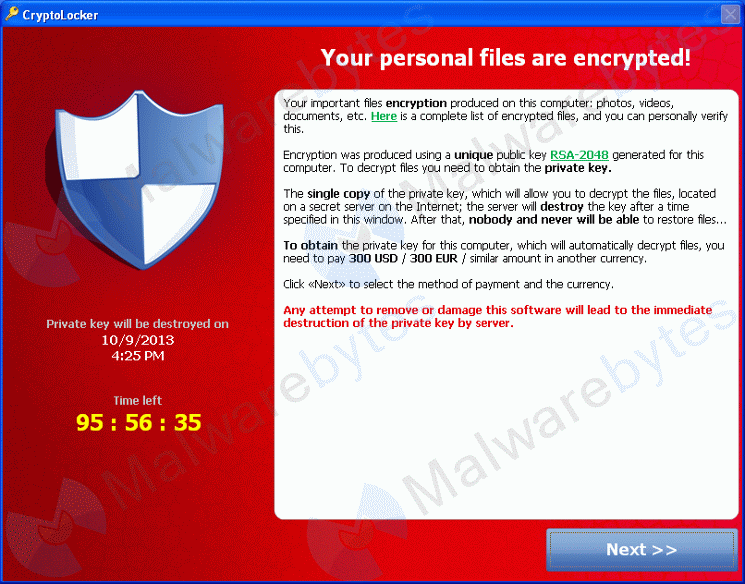 You may have fallen victim to one or more apps we call ‘ransomware’. Ransomware is a type of malware who’s primary purpose is to get you to spend money – let’s just call it extortion. Often, ransomware will lock up at least some of your files, and force you to pay them money to unlock them. This is pretty sneaky, and can be quite destructive. One of the sneakiest is called CryptoLocker. That one takes your files hostage, and forces you to pay money for a ‘private key’ to unlock them. It actually encrypts your personal files, which can only be un-encrypted with the key they’ll sell you.
You may have fallen victim to one or more apps we call ‘ransomware’. Ransomware is a type of malware who’s primary purpose is to get you to spend money – let’s just call it extortion. Often, ransomware will lock up at least some of your files, and force you to pay them money to unlock them. This is pretty sneaky, and can be quite destructive. One of the sneakiest is called CryptoLocker. That one takes your files hostage, and forces you to pay money for a ‘private key’ to unlock them. It actually encrypts your personal files, which can only be un-encrypted with the key they’ll sell you.
November 2013 Update: The US CERT notes that fake UPS and FedEX tracking emails are being used to distribute CryptoLocker, and warns people “experiencing a ransomware infection NOT to respond to extortion attempts by attempting payment and instead to report the incident to the FBI at the Internet Crime Complaint Center (IC3).” We’ve checked this link out and it’s valid. Bad news: if by chance you fell victim to CryptoLocker, your personal files are encrypted and impossible to un-encrypt without paying their ransom – we sincerely hope you backed up your files!
CryptoLocker is most often distributed through email attachments, malicious web pages and websites, and web browser plug-ins that have been compromised. So please be very careful dealing with any of these items!
February 2014 Update: Hackers have extorted over $5M US since the fall of 2013. PowerLocker is a new entry and promises to be even nastier than CryptLocker, and these threats are growing very fast. Worse, we’re seeing signs the perveyors of ransomware are getting organized and turning out packages for purchase by other hackers, leading to a wholesale spread of this insidious threat.
There are lots of different types of ransomware – some identify bogus viruses or other computer infections with a popup message and try to get you to pay to remove them. Of course, the real infection is the ransomware itself. Other types warn you that your computer was used to download illegal files, and try to get you to pay a fine to keep using your computer. In most of these cases, ransomware really gives you nothing for any money you pay, so don’t! Members can read on for more info and recovery help.
But for Pete’s sake, please treat every email you receive with a healthy dose of suspicion – even emails from people you know! Email attachments and hyperlinks in emails are still the most common ways that malware spreads. We all depend on email for day-to-day communication, and the bad guys out there are leveraging our dependence and trust for their own benefit.
So how did you get this ransomware on your computer? For Microsoft Windows PCs, it could have been a simple, inadvertent click on a popup message, ad or link in a web page. The latest versions of Windows have the User Account Control feature to make it harder for bad programs to get installed, but most people either turn off UAC or just click ‘OK’ anytime they get a warning – since Windows throws up warnings all the time.
![]() These programs can be very difficult to remove from your computer, but the most effective method we’ve found is to follow our advice on Tip of the Day #001: Computer Hacked? What to Do! – in particular using Malwarebytes Anti-Malware to scan your PC and remove everything it finds. If you follow all our advice and your system still has ransomware on it, your last resort would be to wipe your hard drive and re-install Microsoft Windows – definitely not a simple fix. We hope you took our advice and also backed up your files, since they will be a) encrypted on your primary hard drive and forever unavailable to you, and b) wiped from your hard drive forever when you reformat the drive to install Windows. And please note that Malwarebytes will not fix a CryptoLocker infection!
These programs can be very difficult to remove from your computer, but the most effective method we’ve found is to follow our advice on Tip of the Day #001: Computer Hacked? What to Do! – in particular using Malwarebytes Anti-Malware to scan your PC and remove everything it finds. If you follow all our advice and your system still has ransomware on it, your last resort would be to wipe your hard drive and re-install Microsoft Windows – definitely not a simple fix. We hope you took our advice and also backed up your files, since they will be a) encrypted on your primary hard drive and forever unavailable to you, and b) wiped from your hard drive forever when you reformat the drive to install Windows. And please note that Malwarebytes will not fix a CryptoLocker infection!
The best solution for a CryptoLocker infection is prevention, and thanks to our friends at SpiceWorks, there is an ‘inoculation’ set of instructions to protect you against CryptoLocker, although most PC security software has protection against this built-in. We’ve looked at their solution and it does work – but it’s primarily for IT experts and businesses to deploy. The link will take you to their website and they ask you to download a zip file, but you can trust us that the zip file is safe.
Inside this zipfile is an Adobe PDF called ‘Cryptolocker Warning.pdf’ that walks both small business system administrators and individuals (starting on page 15) with Microsoft Windows computers through a process of hardening their systems against infection. If you have been infected, look for mitigation instructions starting at the bottom of page 21. For your convenience, we’ve got the warning PDF right here.
This is a pretty involved process – unless you are comfortable editing your System Registry (or don’t even know what I’m talking about), then you might want to hire a professional to help you with this. But be aware that even professionals may be limited in what they can do if CryptoLocker has already encrypted your files – you could end up paying a lot of money for nearly nothing!
Unfortunately, if you didn’t follow our advice to backup your files/computer, and have been infected by CryptoLocker, you have little or no recourse. We recommend you take your lumps and go through the process of formatting your hard drive and installing programs – your personal data files are gone (pictures, documents, etc.). Please do not pay the ransom, it just helps fund the hackers to do more nefarious hacking and you have no guarantee that you’ll even get a working decryption key.
 A word to the wise – avoid ransomware by being diligent at following Safe Computing Practices – we have a handy checklist here. And by all means, do not click on any links in emails, don’t open any email attachments like zip files. Likewise, do not click on any links in webpages that look like ads – especially on websites that aren’t well-known or trusted by many. And even trusted websites can be hacked – just read the newspapers and you’ll know that venerable institutions are being hacked all the time.
A word to the wise – avoid ransomware by being diligent at following Safe Computing Practices – we have a handy checklist here. And by all means, do not click on any links in emails, don’t open any email attachments like zip files. Likewise, do not click on any links in webpages that look like ads – especially on websites that aren’t well-known or trusted by many. And even trusted websites can be hacked – just read the newspapers and you’ll know that venerable institutions are being hacked all the time.
A note about our own website: We use the best protection that we can get, and have an ‘extended validation’ security certificate that shows our URL differently in your web browser’s URL bar than other websites – ours is like banking institutions and other high-security websites. Every page we show you is encrypted between your computer and our web server for maximum security – at a slight cost of slower page loading. We monitor our website constantly both with external tools (like the Sitelock certification you see in the sidebar) and also by using our own tools directly on our webserver. And lastly, while many of our hyperlinks will take you to other websites on the internet, we don’t put a link on our site unless we’ve checked it out to verify that the link doesn’t take you someplace unsafe. We do our absolute best to only point you in ‘right’ directions.
This website runs on a patronage model. If you find my answers of value, please consider supporting me by sending any dollar amount via:
or by mailing a check/cash to PosiTek.net LLC 1934 Old Gallows Road, Suite 350, Tysons Corner VA 22182. I am not a non-profit, but your support helps me to continue delivering advice and consumer technology support to the public. Thanks!







